2018 New Lead2pass Microsoft 70-347 Dumps Free Download:
https://www.lead2pass.com/70-347.html
QUESTION 41
Hotspot Question
Your company uses Office 365 Small Business.
You need to configure the Microsoft Exchange ActiveSync password policy and control the display of presence information.
Which two service categories should you configure on the service settings page of the Office 365 admin portal? To answer, select the appropriate service categories in the answer area.
Answer:
Explanation:
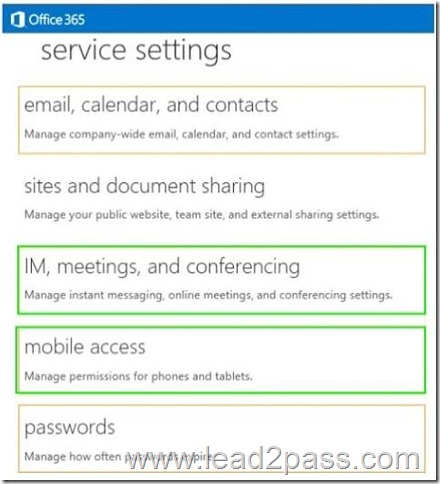
Microsoft Exchange ActiveSync is used to enable mobile phone users to access their email, calendar, contacts, and tasks in an Exchange 2013 or Exchange Online environment. Microsoft Exchange ActiveSync password policy is configured in the Mobile Access section in the Office 365 Service Settings page.
Presence information in Lync Server enables users to approach colleagues at the right time with the right form of communication, to lead to a more productive work environment. A user’s presence is a collection of information that includes availability, willingness to communicate, additional notes (such as location and status), and how the user can be contacted. Presence is enhanced in Lync Server with pictures, location information, and a rich set of presence states that includes “Off Work,” “Do Not Disturb,” and “Be Right Back,” in addition to basic states such as “Available,” “Busy,” and “In a Conference.”
To configure the display of presence information, we need to select the “IM, Meetings and Conferencing” option.
https://technet.microsoft.com/en-us/library/gg417162%28v=ocs.15%29.aspx
QUESTION 42
You are the Office 365 administrator for your company.
The company is running Microsoft Exchange Server 2007 with Service Pack 3 on-premises and has 500 mailboxes.
Management requests that you migrate all mailboxes to Office 365.
You are researching the available migration types.
You need to generate a custom step-by-step checklist for multiple migration types.
Which tool should you use?
A. Exchange Server Deployment Assistant
B. Exchange Best Practices Analyzer
C. Exchange 2013 Server Role Requirements Calculator
D. Microsoft Remote Connectivity Analyzer
Answer: A
Explanation:
The Exchange Server Deployment Assistant is used to help you configure an Exchange Server deployment. It is a web-based tool that asks you questions about your current environment and then generates a custom step-by-step checklist that will help you deploy Exchange Server for different types of scenarios.
The Exchange Server Deployment Assistant asks you questions about your current environment, how many mailboxes you’d like to migrate and which method of migration you’d like to use. You can run the wizard multiple times selecting different options to generate checklists for different migration scenarios.
Incorrect Answers:
B: The Microsoft Exchange Best Practices Analyzer is designed to help you determine the overall health of an existing Exchange server deployment. The tool scans the Exchange servers and topology and identifies items that do not conform to Microsoft best practices. The Exchange Best Practices Analyzer does not generate custom step-by-step checklists for Exchange migrations. Therefore, this answer is incorrect.
C: The Exchange 2013 Server Role Requirements Calculator is a tool used to plan an Exchange server deployment. It is used to help decide how many servers you need and which server roles can be deployed on the same servers or which roles need to be deployed to separate servers. The Exchange 2013 Server Role Requirements Calculator does not generate custom step-by-step checklists for Exchange migrations. Therefore, this answer is incorrect.
D: Microsoft Remote Connectivity Analyzer is a website offered by Microsoft for testing remote connectivity to server services such as Exchange Server, Lync Server and Office 365. Microsoft Remote Connectivity Analyzer does not generate custom step-by-step checklists for Exchange migrations. Therefore, this answer is incorrect.
http://blogs.technet.com/b/blainbar/archive/2014/09/26/part-31-modernizing-your-datacenter-for-hybrid-cloud-migrating-exchange-and-application-servers-to-windows-server-2012-r2.aspx
QUESTION 43
Your company subscribes to the Office 365 Enterprise El plan.
You are the Microsoft Exchange Online administrator.
In the last week, employees have reported that they are receiving non-delivery report messages from other companies.
The employees have not sent messages to recipients within those companies.
You need to prevent non-delivery report messages from reaching employees.
Which content filter option should you turn on in the Exchange admin center?
A. NDR backscatter
B. Conditional Sender ID filtering: hard fail
C. SPF record: hard fail
D. Block all bulk email messages
Answer: A
Explanation:
NDR backscatter is when spammer forges the user’s email address and sends email on their behalf to other recipients. If the “destination mail system” recognizes the mail as a spam or if the mail is sent to non-existing users, the “destination mail system” creates an NDR message that is sent to the organization recipient (the user whose email address was used by the spammer).
http://blogs.technet.com/b/exchange/archive/2014/08/18/spam-email-and-office-365-environment-connection-and-content-filtering-in-eop.aspx
QUESTION 44
You are the Office 365 administrator for Contoso, Ltd.
Some email messages sent from the trusted domain fabrikam.com are being rejected as spam. Some of these email messages originate inside the fabnkam.com network, and some of them originate from an application in the fabrikam.com co-located data center.
The fabrikam.com systems administrators have asked you to add their domain and the IP addresses of the data center that hosts their external application to your list of safe senders.
You need to configure Microsoft Exchange Online Protection.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Configure a content filter to allow the fabrikam.com domain.
B. Configure a mail flow rule to bypass spam filtering for the data center IP address range.
C. Create a connection filter to allow the data center IP address range.
D. Add the fabrikam.com domain as an accepted domain.
E. Create an inbound connector for the fabrikam.com domain.
F. Configure a mail flow rule to bypass spam filtering for the fabrikam.com domain.
Answer: BF
Explanation:
In general, we recommend that you add the IP addresses (or IP address ranges) for all your domains that you consider safe to the IP Allow list. However, if you don’t want your IP Allow List entry to apply to all your domains, you can create a Transport rule that excepts specific domains.
To do this, perform the following steps:
1.In the EAC, navigate to Mail flow > Rules.
2.Click Add Icon and then select Create a new rule. 3.Give the rule a name and then click More options. 4.Under Apply this rule if, select The sender and then choose IP address is in any of these ranges or exactly matches.
5.In the specify IP addresses box, specify the IP address or IP address range you entered in the IP Allow list, click Add Add Icon, and then click ok. 6.Under Do the following, set the action by choosing Modify the message properties and then set the spam confidence level (SCL). In the specify SCL box, select 0, and click ok. 7.Click add exception, and under Except if, select The sender and choose domain is. 8.In the specify domain box, enter the domain for which you want to bypass spam filtering, such as contosob.com. Click Add Add Icon to move it to the list of phrases. Repeat this step if you want to add additional domains as exceptions, and click ok when you are finished.
9.If you’d like, you can make selections to audit the rule, test the rule, activate the rule during a specific time period, and other selections. We recommend testing the rule for a period before you enforce it. Manage mail flow rules contains more information about these selections.
10.Click the save button to save the rule. It appears in your list of rules.
After you create and enforce the rule, spam filtering for the IP address or IP address range you specified is bypassed only for the domain exception you entered.
References:
https://technet.microsoft.com/en-us/library/dn198251(v=exchg.150).aspx
https://technet.microsoft.com/en-us/library/jj200718(v=exchg.150).aspx
QUESTION 45
Drag and Drop Question
You are an Office 365 specialist for a consulting company.
Your company has been hired by several companies to migrate their legacy email solutions to Office 365.
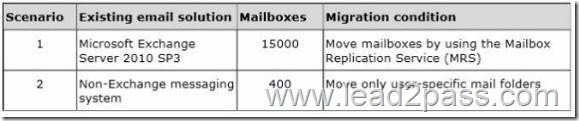
You need to recommend mailbox migration strategies for the scenarios described in the following table.
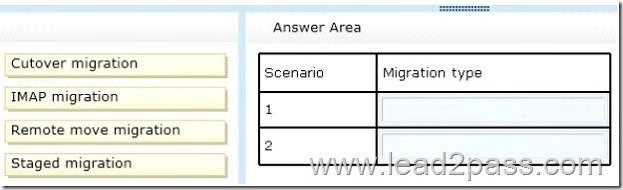
Which strategies should you recommend? To answer, drag the appropriate migration types to the correct targets. Each migration type may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
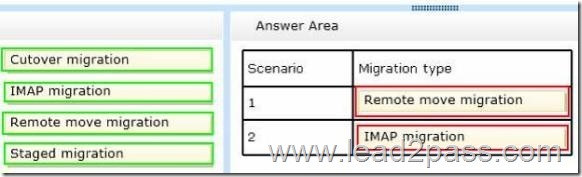
Answer:
Explanation:
For the Microsoft Exchange Server 2010 mailboxes, we can use a remote move migration. When the mailboxes are moved in the remote move operation, the Mailbox Replication Service is used. This is the same service that is used when moving mailboxes between mailbox servers in an on-premise environment. In this question, the Exchange on-premise and Exchange Online environments will be configured in a hybrid configuration. That will enable us to move mailboxes to Exchange Online in the same way you would move a mailbox to another local mailbox server.
A remote move migration is used to migrate on-premises Exchange mailboxes to Exchange Online in an Exchange hybrid deployment. You must have an Exchange hybrid deployment to use a remote move migration. With a hybrid deployment, you get the following capabilities:
User account management in your on-premises organization.
Directory synchronization between your on-premises and Exchange Online organizations.
Single sign-on to mailboxes located either on-premises or in the Exchange Online organization.
Secure mail routing between on-premises and Exchange Online organizations.
Free/busy and calendar sharing between on-premises and Exchange Online organizations.
For a non-Exchange messaging system, the only migration option available is the IMAP migration.
In an IMAP migration, the contents of users’ mailboxes on an IMAP messaging system are migrated to their Exchange Online mailboxes. Here are some requirements and considerations for using an IMAP migration:
The Exchange Online mailboxes that you migrate email to must already exist. They aren’t provisioned during the IMAP migration process.
Only items in a user’s inbox or other mail folders are migrated. Contacts, calendar items, or tasks aren’t migrated.
Small and medium-sized organizations can use an IMAP migration to migrate email from mailboxes on a hosted service provider.
Incorrect Answers:
Cutover migration: In a cutover migration, all mailboxes are moved in a single batch. A cutover migration should be used for less than 2,000 mailboxes. A cutover migration is not supported for non-Exchange mailboxes. Therefore, this answer is incorrect.
Staged migration: A staged migration requires Exchange 2003 or Exchange 2007. It is not supported with Exchange 2010 or non-Exchange mailboxes. Therefore, this answer is incorrect.
https://technet.microsoft.com/en-GB/library/jj863291(v=exchg.150).aspx
QUESTION 46
You are the Microsoft Lync administrator for a company that uses Lync Online.
The company has mandated that employees may use Lync Online to communicate with contacts from approved external domains.
You need to configure Lync Online to allow Lync federation with only three specific domains.
You must achieve this goal by using the least amount of administrative effort.
Which two actions should you perform? Each correct answer presents part of the solution.
A. In the Lync admin center, set the External Access option to On except for blocked domains.
B. In the Office 365 admin center, add the three domains to the domain list and set the domain
intent for each domain to Lync Online.
C. In the Lync admin center, set the External Access option to Off completely.
D. In the Lync admin center, set the External Access option to On only for allowed domains.
E. In the Lync admin center, configure the Presence Privacy Mode option to display presence
information only to the users’ contacts.
F. In the Lync admin center, add the three domains to the Blocked Or Allowed Domains list.
Answer: DF
Explanation:
http://solveit.openjive.com/post/2014/01/27/Lync-Federation-with-Office-365Lync-Online
http://technet.microsoft.com/en-us/library/hh852512.aspx
http://technet.microsoft.com/en-us/library/jj205126.aspx
70-347 dumps full version (PDF&VCE): https://www.lead2pass.com/70-347.html
Large amount of free 70-347 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDTmZ1RjZSYlV3V00
You may also need:
70-346 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDVjBwLTI5aDNwM1k