Lead2pass New Released Microsoft 70-744 Exam Questions From Microsoft Exam Center:
https://www.lead2pass.com/70-744.html
QUESTION 1
Note: This question is part of a series of question that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is Independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1 that runs Windows Server 2016.
Server1 has a volume named Volume1.
Dynamic Access Control is configured. A resource property named Property1 was created in the domain.
You need to ensure that Property1 is set to a value of Big for all of the files in Volume1 that are larger than 10 MB.
Which tool should you use?
A. File Explorer
B. Shared Folders
C. Server Manager
D. Disk Management
E. Storage Explorer
F. Computer Management
G. System Configuration
H. File Server Resource Manager (FSRM)
Answer: H
Explanation:
In FSRM, “Large Files” creates a list of files conforming to a specified file spec that are a specified size or larger.
QUESTION 2
Note: This question is part of a series of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to It. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com.
All servers run Windows Server 2016. The forest contains 2,000 client computers that run Windows 10.
All client computers are deployed (rom a customized Windows image.
You need to deploy 10 Pnvileged Access Workstations (PAWs).
The solution must ensure that administrators can access several client applications used by all users.
Solution: You deploy 10 physical computers and configure each wie as a virtualization host.
You deploy the operating system on each host by using the customized Windows image.
On each host you create a guest virtual machine and configure the virtual machine as a PAW.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 3
Your network contains an Active Directory forest named contoso.com.
The forest functional level is Windows Server 2012. All servers run Windows Server 2016.
You create a new bastion forest named admin.contoso.com.
The forest functional level of admin.contoso.com is Windows Server 2012 R2.
You need to implement a Privileged Access Management (PAM) solution.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Raise the forest functional level of admm.contoso.com.
B. Deploy Microsoft Identify Management (MIM) 2016 to admin.contoso.com.
C. Configure contoso.com to trust admin.contoso.com.
D. Deploy Microsoft Identity Management (MIM) 2016 to contoso.com.
E. Raise the forest functional level of contoso.com.
F. Configure admin.contoso.com to trust contoso.com.
Answer: BC
QUESTION 4
Your network contains an Active Directory domain named conioso.com.
The domain contains 1,000 client computers that run Windows 8.1 and 1,000 client computers that run Windows 10.
You deploy a Windows Server Update Services (WSUS) server.
You create a computer group tor each organizational unit (OU) that contains client computers.
You configure all of the client computers to receive updates from WSUS.
You discover that all of the client computers appear m the Unassigned Computers computer group in the Update Services console.
You need to ensure that the client computers are added automatically to the computer group that corresponds to the location of the computer account in Active Directory.
Which two actions should you perform? Each correct answer presents part of the solution.
A. From Group Policy objects (GPOs), configure the Enable client-side targeting setting.
B. From the Update Services console, configure the Computers option.
C. From Active Directory Users and Computers, create a domain local distribution group for each WSUS computer group.
D. From Active Directory Users and Computers, modify the flags attnbute of each OU.
E. From the Update Services console, run the WSUS Server Configuration Wizard.
Answer: AB
QUESTION 5
Note: This question Is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is Independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2016.
Server1 has a shared folder named Share1.
You need to encrypt the contents of Share1.
Which tool should you use?
A. File Explorer
B. Shared Folders
C. Server Manager
D. Disk Management
E. Storage Explorer
F. Computer Management
G. System Configuration
H. File Server Resource Manager (FSRM)
Answer: C
Explanation:
You can encrypt files from > file and storage services > share > properties of the folder and then setting, there is an encrypt data access checkbox which is unchecked by default.
QUESTION 6
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains an Active Directory domain named contoso.com.
The functional level of the forest and the domain is Windows Server 2008 R2.
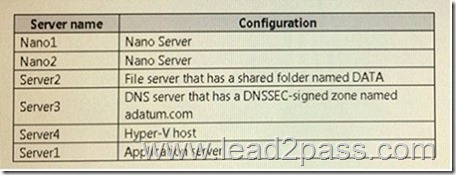
The domain contains the servers configured as shown in the following table.
All servers run Windows Server 2016. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department.
You have an OU named Finance that contains the computers in the finance department.
You have an OU named AppServers that contains application servers.
A Group Policy object (GPO) named GP1 is linked to the Marketing OU.
A GPO named GP2 is linked to the AppServers OU.
You install Windows Defender on Nano1.
End of repeated scenario
You need to ensure that you can deploy a shielded virtual machine to Server4.
Which server role should you deploy?
A. Hyper-V
B. Device Health Attestation
C. Network Controller
D. Host Guardian Service
Answer: D
Explanation:
A guarded fabric consists of:
1 host guardian service (hgs)
1 or more guarded hosts (in this case Server4)
A set of shielded VMs.
https://technet.microsoft.com/en-us/windows-server-docs/security/guarded-fabric-shielded-vm/guarded-fabric-and-shielded-vms
QUESTION 7
Your network contains an Active Directory domain named contoso.com.
The domain contains four servers.
The servers are configured as shown in the following table.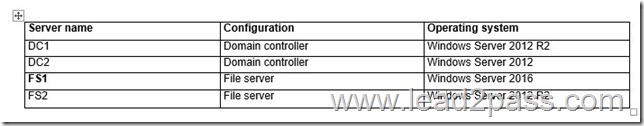
You need to manage FS1 and FS2 by using Just Enough Administration (JEA).
What should you do before you can implement JEA?
A. Install Microsoft .NET Framework 4.6.2 on FS2.
B. Install Microsoft .NET Framework 4.6.2 on FS1.
C. Install Windows Management Framework 5.0 on FS2.
D. Upgrade FS2 to Windows Server 2016.
Answer: C
Explanation:
JEA is incorporated into Windows Server 2016 and Windows 10, and is also incorporated into Windows Management Framework 5.0, which you can download and install on computers running Windows Server 2012 R2.
QUESTION 8
Your network contains an Active Directory domain named contoso.com.
You are deploying Microsoft Advanced Threat Analytics (ATA).
You create a user named User1.
You need to configure the user account of User1 as a Honeytoken account.
Which information must you use to configure the Honeytoken account?
A. the SAM account name of User1
B. the Globally Unique Identifier (GUID) of User1
C. the SID of User1
D. the UPN of User1
Answer: C
Explanation:
To configure a Honeytoken user you will need the SID of the user account, not the user name.
https://docs.microsoft.com/en-us/advanced-threat-analytics/deploy-use/working-with-detection-settings
70-744 dumps full version (PDF&VCE): https://www.lead2pass.com/70-744.html
Large amount of free 70-744 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDVExYaWZyTWt4OGc
You may also need:
70-740 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDMXFQVl9VSWx5WGs
70-741 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDb05IRmRaei1JLVE
70-742 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDRWlFSW1vN0JwT3M
70-743 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDdjVzVlJxOXB5TTg